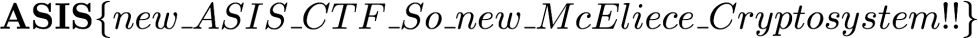ASIS Quals 2017 – Alice, Bob, and Rob – 202 points
Description:
We have developed a miniature of a crypto-system. Can you break it?
We only want to break it, don’t get so hard on our system!
Here is the file.
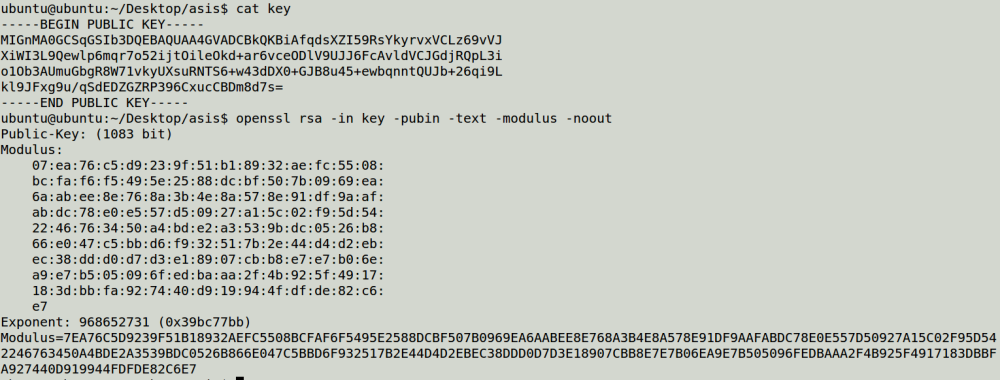
There are 3 files: source code encrypt.py, encrypted file flag.enc, key flag.pub.
The algorithm is so easy, read 1 byte/time then compute it and ouput 2 bytes. The encrypt algorithm is just convert the 1-byte-plaintext into 2 matrixs then compute the products of the plaintext matrix and the key matrix. The result will be change 1 bit then save as output.
1-byte was encrypted with 4 bits plaintext. We can reverse the algorithm by check all of plaintext available (16 value). We can guess the plaintext by compute the product of the 4-bit plaintext and the key, if the result is different 1 bit with the encrypted byte, then it maybe the correct plaintext with this encrypt byte.
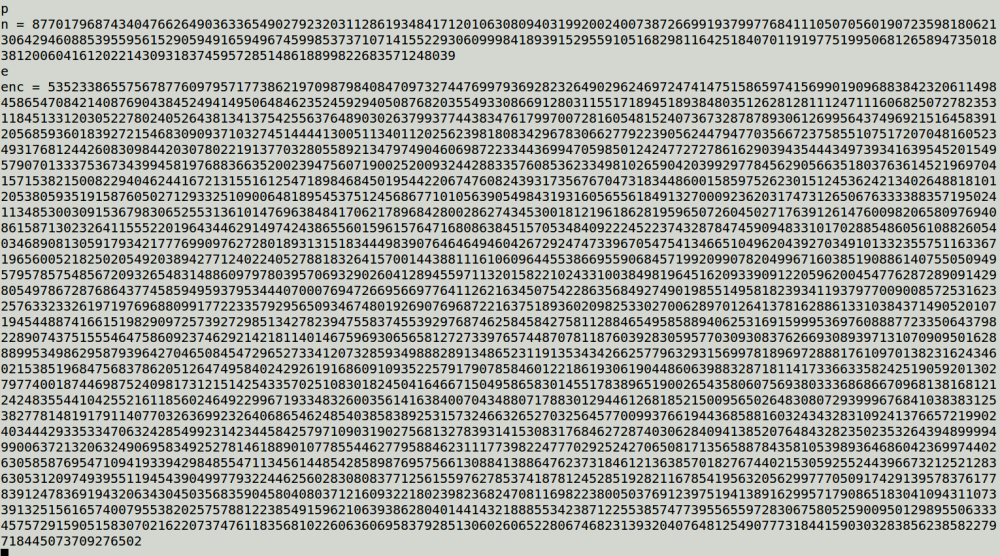
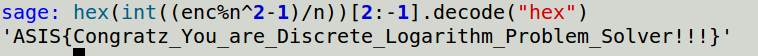
Here my sage script.
And here is my result.